How to set up smart host (mail relay) services to work with Sigsync service
Problem:
When using the Sigsync service in conjunction with third-party smart host services like
Proofpoint
Barracuda
Mimecast
Reflexion, and other similar solutions, you might encounter situations where an email is sent without the signature being applied.
Solution:
Follow the below steps to set up smart host (mail relay) services to work with Sigsync service.
Step 1: Ensure Sigsync Azure service Exchange transport rule priority is set to top
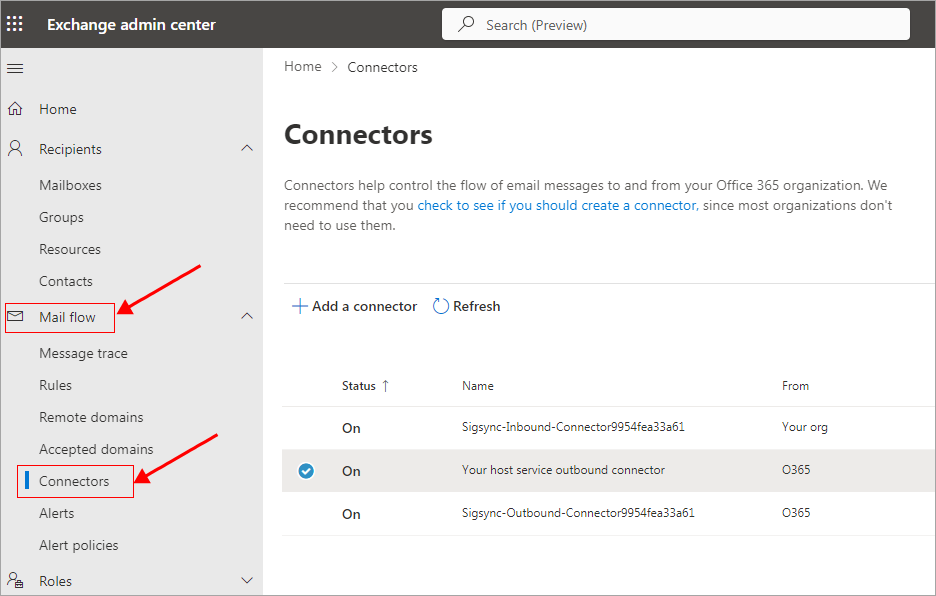
- Step 1: Login to Exchange admin center (EAC)
- Step 2: Navigate to the 'Mail flow’ > ’ Rules’ tab.
- Step 3: Ensure that the Sigsync Transport rule is assigned the highest priority by confirming its placement at the top of the list.
- Step 4: If you are operating in a hybrid environment where your on-premise Exchange environment handles message relaying, it is recommended to transfer this responsibility to Office 365.
Step 2: Reconfigure the outbound connector of the third-party smart host service
To set up the control of the outbound connector for your smart host service using an Exchange transport rule, follow the below steps:
- Step 1: Log in to the Office 365 portal using your global administrator credentials and locate the 'Admin' icon.
- Step 2: Click 'Show all' open the Admin centers and then navigate to the 'Exchange' tab
- Step 3: Navigate to the ‘Mail flow’ > ‘Connectors’ tabs
- Step 4: Select your smart host service outbound connector
- Step 5: Click the ‘Edit use’ under the ‘Use of connector’.
- Step 6: Any domains listed under the condition ‘Only when email messages are sent to these domains’, you will need to replicate these settings when setting up a new transport rule that will manage this connector, as explained in the next section.
- Step 7: Select the option ‘Only when I have a transport rule set up that redirects messages to this connector’.
- Step 8: You will be prompted for the validation email. Once it is successful, click the ‘Save’ button to save changes to the connector.
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 3: Create or edit a transport rule for a smart host and set the conditions for senders and recipients
- Step 1: Login to the Office 365 portal as a global administrator and click the ‘Admin’ icon
- Step 2: Click ‘Show all’ and select the ‘Exchange’ tab.
- Step 3: Navigate to the ‘Mail flow’ > ‘Rules’ tabs
- Step 4: Click the '+ Add a rule' button and select ‘Create a new rule’ from the drop down list
- Step 5: Give an appropriate name for the smart host rule.
- Step 6: Under ‘Apply this rule if’, select ‘The sender’ and ‘is external / internal’ from the dropdown list
- Step 7: Select ‘Inside the organization’ and click the ‘Save’ button . This will ensure that all emails sent from your Office 365 tenant are routed through the connector.
- Step 8: Click the ‘+’ icon to add another condition and select ‘The recipient’ and ‘is external / internal’.
- Step 9: Select ‘Outside the organization’ and click the ‘Save’ button . This ensures internal email sent from your Office 365 tenant will be routed through the connector by avoiding mail loops.
- Step 10: If you previously configured your connector to operate exclusively when emails are sent to specific domains (as outlined in the previous section), it is essential to replicate this behavior in the current setup. To achive this, click the ‘+’ icon and select ‘The recipient’ and ‘address matches any of these text patterns’.
- Step 11: Enter the domain name and click the ‘Add’ button. ‘Save’ the changes.
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 4: Add the custom headers into the message and redirect it to the appropriate connector
To prevent message looping even if your smart host sends the message back to EOP (Exchange Online Protection), follow these steps to add message headers:
- Step 1: To distinguish the mail using the header information, add an action in the ‘Do the following’ section by selecting ‘Modify the message properties’ and ‘set a message header’.
- Step 2: Click the ‘Enter text’ link to set the message header
- Step 3: Enter the message header and click the ‘Save’ button.
For Example, message header text can be 'X-Smart_Host-Processed'. - Step 4: Click the ‘Enter text’ link to set message header value
- Step 5: Enter the value for message header
- Step 6: Click the ‘+’ icon to add an action in the ‘Do the following...’ section and select ‘Redirect the message to’ and ‘the following connector’
- Step 7: Select the outbound connector of your smart host and click the ‘Save’ button
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 5: Add an exception based on the message header created in the above steps to avoid message looping
- Step 1: Under the ‘Except if’ section add a new exception by selecting ‘The message headers…’ and ‘includes any of these words’.
- Step 2: Click the ‘Enter Text’ link to add the message header
- Step 3: Enter the same name (For Example, message header text is 'X-Smart_Host-Processed') for the message header as you have used in the previous step and click the ‘Save’ button
- Step 4: Click the ‘Enter words’ link to set the value to the message header
- Step 5: Enter the message header value as ‘yes’ and click the ‘Add’ button and ‘Save’ the changes
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 6: Navigate to the 'Set rule settings' and save the changes to the rule
Proceed to the next step by clicking ‘Next’ to navigate to the ‘Set rule settings’ section.
- Step 1: Proceed to the next step by clicking ‘Next’ to navigate to the ‘Set rule settings’ section.
- Step 2: Enable the option ‘Defer the message if rule processing doesn't complete’. After this option is enabled, your message will persistently attempt to utilize the smart host, even if the previous attempt was unsuccessful. Click the ‘Next’ button to proceed to the ‘Review and finish’ step.
- Step 3: Click the ‘Finish’ button to complete the rule creation process
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 7: Enable the newly created/edited smart host transport rule
- Once you have created the rule, it will be placed at the bottom of the rules list with the lowest priority. By default, the rule will be disabled. To ensure the desired placement, select the new rule and click the ‘Move up’ button to position below the Sigsync Exchange transport rule.By default, Sigsync Rule has a priority of ‘0’. To maintain the desired order, assign a priority of ‘1’ to your smart host rule shown in the screenshot below. You can also manually adjust the rule's priority if needed. Lastly, Select the smart host rule and activate it by toggling the switch to the ‘Enabled’ position.
Note: If you have multiple outbound connectors for smart hosts, you will need to repeat the entire procedure for each connector.
Step 8: Modify the Exchange transport rule for the Sigsync Azure service
Once you have configured the transport rules for the third-party host connectors, the next step is to configure the transport rules for Sigsync. This final configuration is important to ensure the proper routing of all email messages.
Note: It is important to ensure that after an email is sent, it first reaches the Sigsync Azure Service before any other rule takes precedence. To accomplish this, select the 'Stop processing more rules' option, which guarantees that the Sigsync transport rule is the only rule applied, as long as it has the highest priority of 0 (zero).
Once the signature is added, the email is routed back from the Sigsync Azure email service to Exchange Online Protection. At this stage, the Sigsync transport rule is not executed again, rendering the 'Stop processing more rules' option invalid. Consequently, any other rules configured for your tenant will now be executed.- Step 1: Click the ‘Sigsync Routing Rules’.
- Step 2: Select the ‘Edit Rule Settings’ tab
- Step 3: Check ‘Stop processing more rules’ and click the ‘Save’ button to save the rule changes. This guarantees that Sigsync processes all the emails and adds Signature to it and then the Security service processes the email to make it secure.
Your Office 365 setup is now complete! You can send an email to test the flow and analyze it using message trace and also analyze message header.
Note: If you are still encountering mail flow issues even after following the steps mentioned above, we recommend analyzing the mail headers to verify if the emails are being routed to Sigsync services as the first troubleshooting step. You can find detailed instructions on how to view message headers in Outlook by clicking here.
Additionally, please note that changes made to smart host transport rules may take some time to propagate. It is important to wait for approximately an hour or so for the changes to take effect.
If you require any assistance in setting up a smart host that is compatible with Sigsync, we highly recommend reaching out to Sigsync support for further guidance and support.
Streamline Email Signature Management with a Free On-demand Demo from Sigsync
Sigsync email signature service provides effortless, centralized signature management for Office 365 and Exchange. Our team can assist you in quickly setting up company-wide signatures. Request a free on-demand demo to see how Sigsync can simplify your email signature management process.